Do more
with where
We built the golden triangle—precise location, device, and behavioural intelligence that gives you a high-res picture of digital trust. Put it into action to delight your good customers with safe, seamless, silent verification while stopping fraud in real-time.
Trusted by industry leaders

See how GeoComply’s solutions keep you one step ahead of fraud
Gaming
Your one-stop shop for anti-fraud, geolocation compliance, and KYC. Serving the U.S. and global gaming markets.
Learn MoreFinancial Services + Crypto
Mitigate fraud, AML, and sanctions risks by authenticating a user’s true location and device integrity.
Learn MoreMedia & Entertainment
Stop geo-piracy with accurate VPN detection to ensure your exclusive content stays exclusive.
Learn More
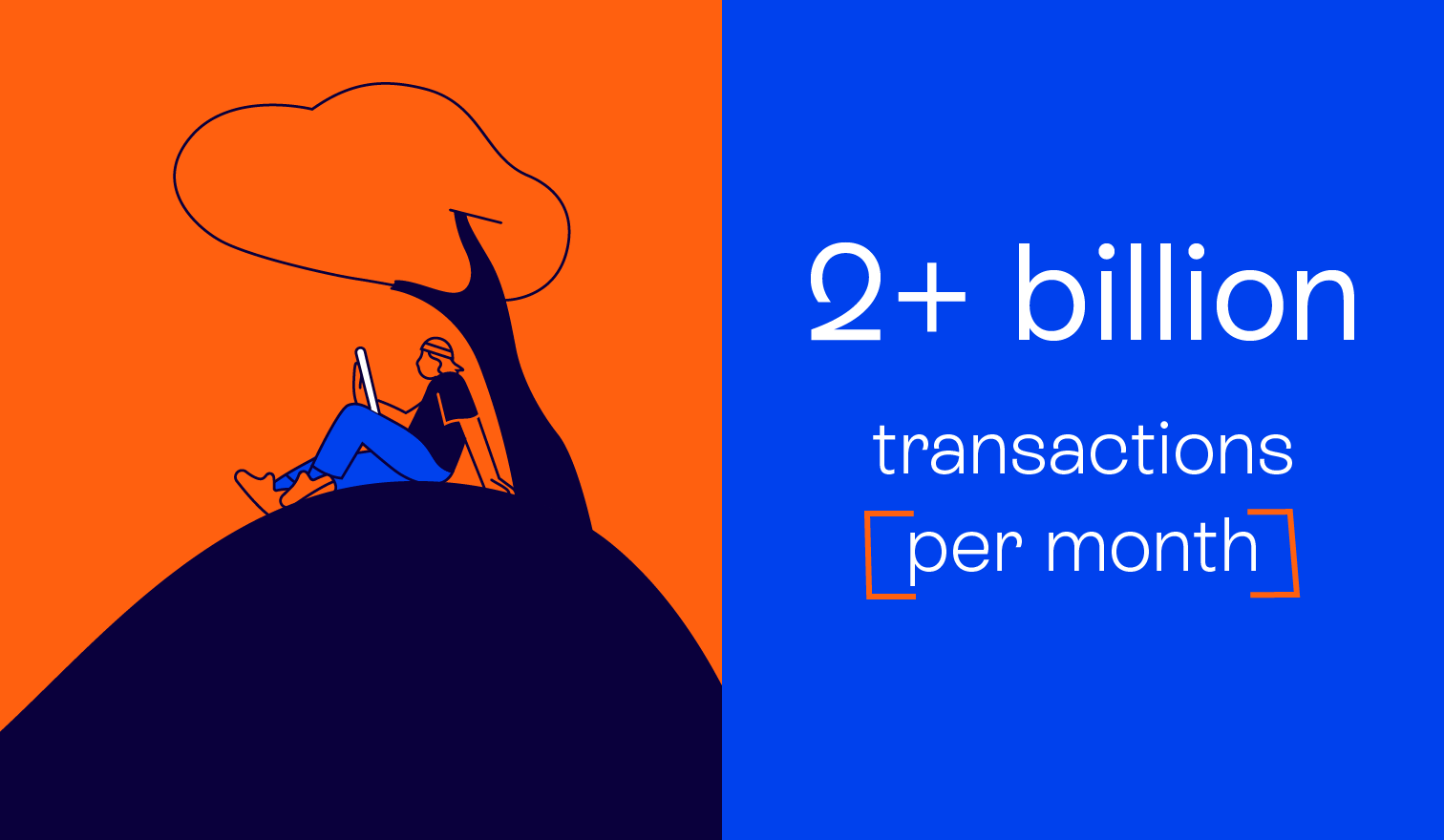
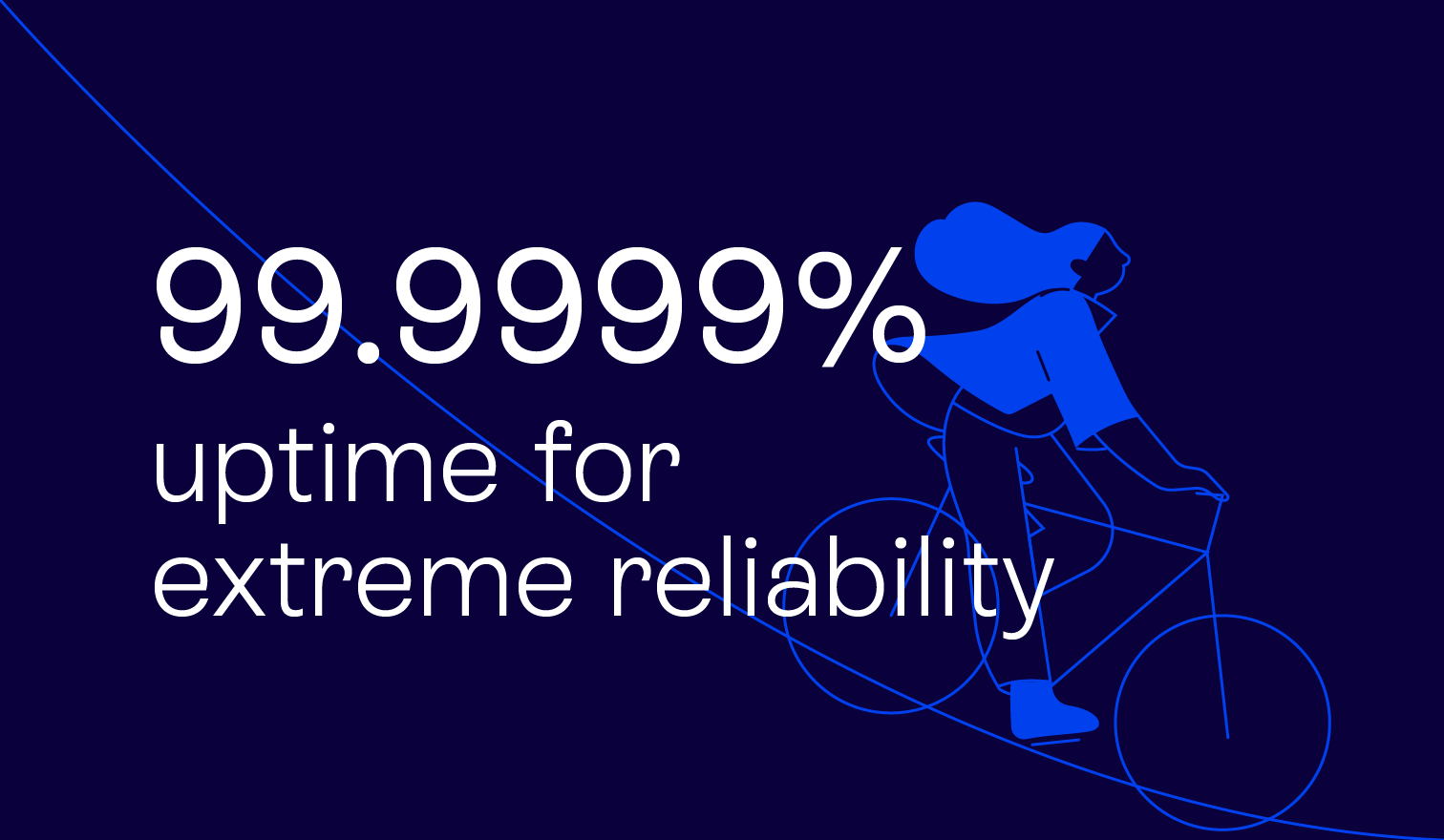

Understand the risk of every online interaction
Fraudsters fake locations and tamper with devices. GeoComply spots and stops them with lightning-fast, advanced integrity checks. Now, you can trust your users are who and where they say they are, safeguarding your business from millions in potential fraud losses and non-compliance penalties.
On-property geofencing tailored for you
PinPoint combines proprietary beacon technology with our core geolocation compliance software to create custom virtual boundaries. Tell us what you need to geofence; PinPoint makes it happen.
Boost your chargeback win rate by up to 90%
When a customer claims they didn’t shop online or place a bet, our compelling evidence reports prove they did. In-depth evidence – a combination of device integrity and geolocation history – plus end-to-end chargeback management help you win disputes.
Identify location fraud with award-winning VPN and proxy detection
Geo-piracy and sanctions risks have one thing in common – they both involve IP address spoofing. GeoGuard is a continually updated IP database that detects and flags anonymizers such as VPNs, proxies, and Tor exit nodes. The result? Lower fraud and compliance risks.